BumbleBee notes 🐝
— pboBumbleBee is categorized as a Loader, the malware is used by Initial Access Brokers to gain access in targeted companies. This article aims to summarizing the different TTPs observed in campaigns distributing BumbleBee and provides a script to extract its configuration.

TL;DR BumbleBee #
The loader delivers diverse payloads (e.g: Cobalt Strike, ransomware, etc), the operators of BumbleBee have been named EXOTIC LILY by the TAG in a report published in March 2022. Google TAG article mentionned BumbleBee Loader (e.g: The user-agent set to bumblebee, hence dubbed BUMBLEBEE. https://blog.google/threat-analysis-group/exposing-initial-access-broker-ties-conti/ Moreover, similarities with other loaders in terms of operation have been noticed notably with IcedID and Emotet. Code similarty (hook installation) with Trickbot have been observed and explained in the post The chronicles of Bumblebee: The Hook, the Bee, and the Trickbot connection. The malware is well documented by now (March 2023) as evidenced by the number of reports on malpedia.
BumbleBee capabilities #
The malware has a custom unpacking mechanism, it manipulates hooks to setup its execution chain, the loader uses multiple environment detection techniques because of the complete integration of the project al-khaser al-khaser is a PoC “malware” application with good intentions that aims to stress your anti-malware system. It performs a bunch of common malware tricks with the goal of seeing if you stay under the radar. . It communicates with its command and control over HTTP. Since August 2022 the malware embeds a list of IP addresses in its configuration, some of them are legitimate IP addresses, this technique is also used by other malware such as Emotet and Trickbot.
BumbleBee command and control IP addresses, port and the bot (or botnet) identifier are stored in the .data section, obfuscated with the RC4 encryption algorithm. A script to extract and deobfuscate
them is provided at the end of this post.
Campaigns file format #
First malspam campaign which delivered BumbleBee contains a web link to a protected ZIP archive.
- The archive contains an ISO file;
- The ISO contains a LNK file and a DLL file;
- The LNK executes
rundll32.exeto invoke the embedded DLL;
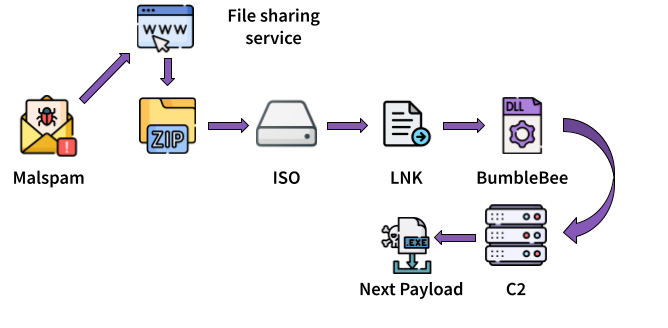
Figure 1: BumbleBee infection chain with ISO file
This model of campaign was used for months. During the summer of 2022, actors updated the disk image format from ISO to VHD.
Content of disk image (VHD) changed too, the DLL is no more stored as a file, but it is embed obfuscated in a PowerShell script. The script is executed by
the LNK with the execution policy set to bypass. The BumbleBee’s DLL is stored in the PowerShell script in obfuscated strings (e.g: $elem30=$elem30.$casda.Invoke(0,"H")).
After strings replacement, the base64 encoded variable is decoded, decrompressed (ungzip) and invoked (e.g: scriptPath | iex).
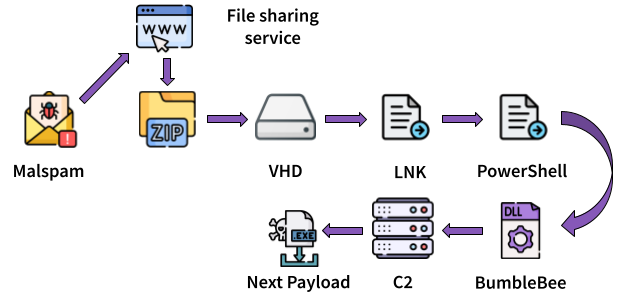
Figure 2: BumbleBee infection chain with VHD file
NB: File sharing service used to deliver BumbleBee change regulary e.g.: WeTransfer, Onedrive, Smash, etc. Details of a campaign using onedrive file sharing website are written in the article: Bumblebee DocuSign Campaign.
Examples IOCs:
- ISO: SHA-256: 8695f4936f2942d322e2936106f78144f91602c7acace080e48c97e97b888377
- VHD: SHA-256: e9a1ce3417838013412f81425ef74a37608754586722e00cacb333ba88eb9aa7
Configuration extractor #
As introduced above, the configuration is stored encrypted with the RC4 algorithm. RC4: Rivest Cipher 4, also known as ARC4: https://en.wikipedia.org/wiki/RC4 The key is in cleartext in the binary and its length is repeatedly (for BumbleBee case) fixed to 10 characters.
Here is the two functions that implement RC4 algorithm in BumbleBee:
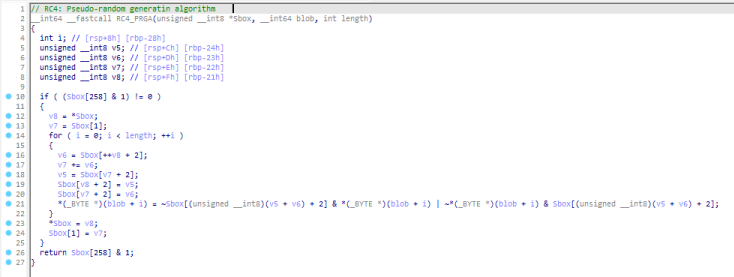
Figure 3: BumbleBee implemenation of PRGA of RC4 algorithm
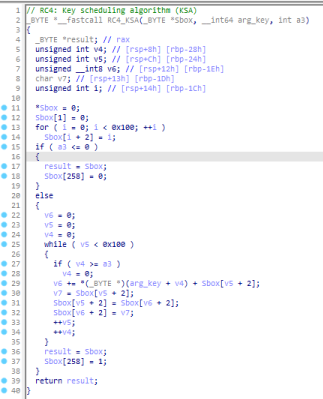
Figure 4: BumbleBee implementation of KSA of RC4 algorithm
The key is stored at the end of the blob of data containing the encrypted list of IP addresses. After analysing few samples of BumbleBee, it appears that the blob of data containing the IP addresses is always 4105 bytes long (plus one null byte) which is a pattern to look for in the DLL for a C2 extractor.
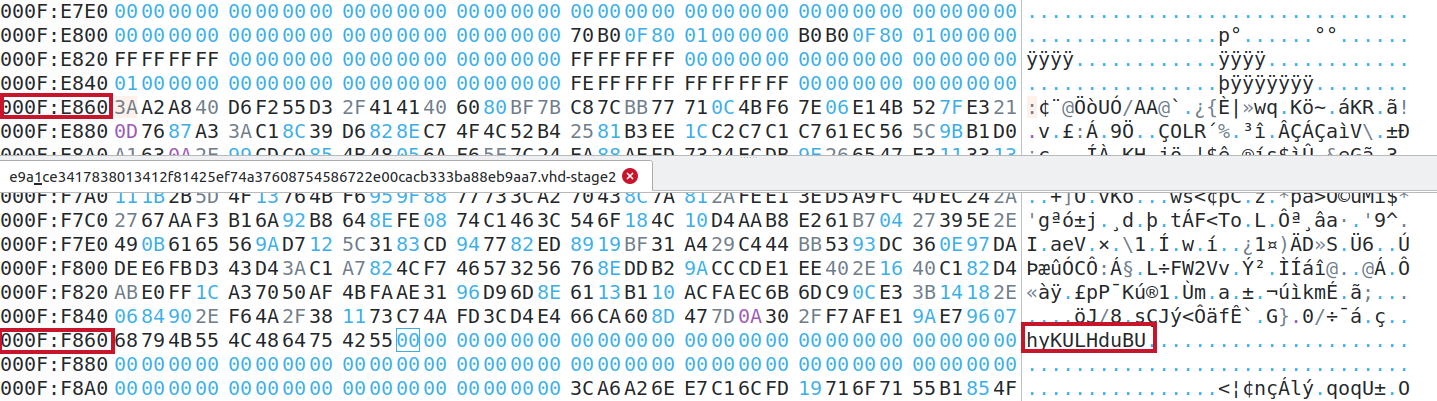
Figure 5: Location of the blob and the RC4 key
The script below attempts to loop over data until a blob matches the blob size, then it extracts the RC4 key (the last 10 bytes of the blob) to finally decrypt the data.
|
|
PS: Tested with the package cryptography with the version: 3.4.8.
Go head and re-use, adapt the script for your needs!
Resources #
- https://blog.google/threat-analysis-group/exposing-initial-access-broker-ties-conti/
- https://elis531989.medium.com/the-chronicles-of-bumblebee-the-hook-the-bee-and-the-trickbot-connection-686379311056
- https://malpedia.caad.fkie.fraunhofer.de/details/win.bumblebee
- https://0xtoxin-labs.gitbook.io/malware-analysis/malware-analysis/bumblebee-docusign-campaign